- 浏览: 948649 次
-

文章分类
最新评论
借出数码相机,还回两只“蠕虫”(worm)
一个朋友还来借用已久的数码相机,正好偶家后院的一些花开得正盛,于是拍了几张PP,然后导入电脑处理。
偶打开WinRAR作例行检查,打开相机记忆棒对应的L盘,不由吓出了一身冷汗,发现两个伪装成文件夹的EXE病毒文件,还多出一个名为recycled、类似回收站的文件夹,瑞星居然没有反应!
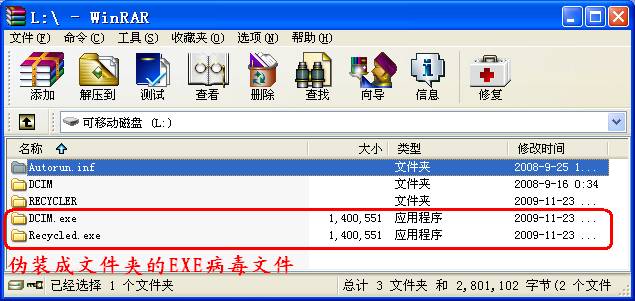
难道遇到了瑞星检测不出来的病毒?
在“资源管理器”中打开L盘,
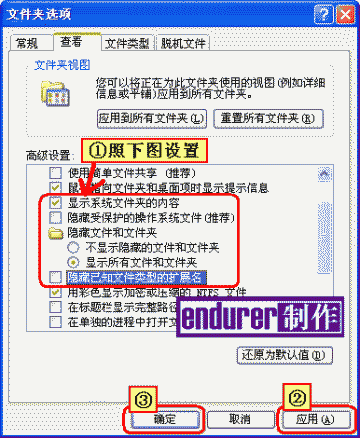
进入 工具-》文件夹选项,取消“隐藏受保护的操作系统文件”和“隐藏已知文件类型的扩展名”前的钩,并选择“显示所有文件和文件夹”,应用,确定。
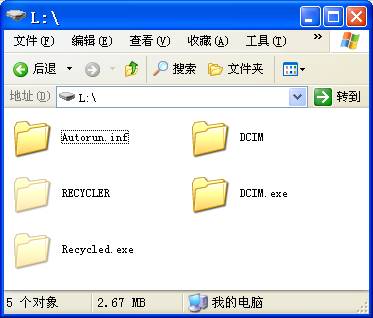
在DCIM.EXE上按右键,从快捷菜单中选择“使用瑞星杀毒”,瑞星才检测出Worm.Win32.Autorun.eyr!
用FileInfo提取病毒文件信息:
文件说明符 : L:/DCIM.exe
属性 : A---
数字签名:否
PE文件:是
获取文件版本信息大小失败!
创建时间 : 2009-11-23 10:47:43
修改时间 : 2009-11-23 10:47:48
大小 : 1400551 字节 1.343 MB
MD5 : d7435879a170e839eeeadb9587d68981
SHA1: 9A3727F6A25D14677840D6D578B4B6D1A1C3EC34
CRC32: b68180f7
上传到 http://www.virustotal.com扫描,结果如下:
| 反病毒引擎 | 版本 | 最后更新 | 扫描结果 |
| a-squared | 4.5.0.43 | 2009.12.15 | Trojan.Win32.FlyStudio!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.12.15 | Win-Trojan/Zahl3731763.1400551 |
| AntiVir | 7.9.1.108 | 2009.12.15 | TR/Dropper.Gen |
| Antiy-AVL | 2.0.3.7 | 2009.12.15 | - |
| Authentium | 5.2.0.5 | 2009.12.02 | W32/Nuj.A.gen!Eldorado |
| Avast | 4.8.1351.0 | 2009.12.15 | Win32:Trojan-gen |
| AVG | 8.5.0.427 | 2009.12.15 | SHeur2.FZD |
| BitDefender | 7.2 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| CAT-QuickHeal | 10.00 | 2009.12.15 | TrojanDropper.Silly.b |
| ClamAV | 0.94.1 | 2009.12.15 | - |
| Comodo | 3251 | 2009.12.15 | UnclassifiedMalware |
| DrWeb | 5.0.0.12182 | 2009.12.15 | Win32.HLLW.Autoruner.4360 |
| eSafe | 7.0.17.0 | 2009.12.14 | - |
| eTrust-Vet | 35.1.7176 | 2009.12.15 | - |
| F-Prot | 4.5.1.85 | 2009.12.14 | W32/Nuj.A.gen!Eldorado |
| F-Secure | 9.0.15370.0 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| Fortinet | 4.0.14.0 | 2009.12.15 | PossibleThreat |
| GData | 19 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| Ikarus | T3.1.1.74.0 | 2009.12.15 | Trojan.Win32.FlyStudio |
| K7AntiVirus | 7.10.920 | 2009.12.14 | Trojan.Win32.Malware.4 |
| Kaspersky | 7.0.0.125 | 2009.12.15 | Worm.Win32.FlyStudio.bt |
| McAfee | 5832 | 2009.12.14 | W32/Autorun.worm.ev |
| McAfee+Artemis | 5832 | 2009.12.14 | W32/Autorun.worm.ev |
| McAfee-GW-Edition | 6.8.5 | 2009.12.15 | Trojan.Dropper.Gen |
| Microsoft | 1.5302 | 2009.12.15 | Backdoor:Win32/FlyAgent.F |
| NOD32 | 4689 | 2009.12.15 | Win32/AutoRun.FlyStudio.CC |
| Norman | 6.04.03 | 2009.12.15 | W32/Lineage.BPWK |
| nProtect | 2009.1.8.0 | 2009.12.15 | Trojan/W32.Agent.1400551 |
| Panda | 10.0.2.2 | 2009.12.14 | Generic Malware |
| PCTools | 7.0.3.5 | 2009.12.15 | Net-Worm.SillyFDC |
| Prevx | 3.0 | 2009.12.15 | High Risk Worm |
| Rising | 22.26.01.01 | 2009.12.15 | Worm.Win32.Autorun.eyr |
| Sophos | 4.48.0 | 2009.12.15 | Mal/Behav-004 |
| Sunbelt | 3.2.1858.2 | 2009.12.15 | Trojan.Win32.Generic!BT |
| Symantec | 1.4.4.12 | 2009.12.15 | W32.SillyFDC |
| TheHacker | 6.5.0.2.093 | 2009.12.15 | W32/FlyStudio.bt |
| TrendMicro | 9.100.0.1001 | 2009.12.15 | TROJ_DROPPER.GEP |
| VBA32 | 3.12.12.0 | 2009.12.13 | Trojan-Dropper.Win32.Flystud.ko |
| ViRobot | 2009.12.15.2089 | 2009.12.15 | - |
| VirusBuster | 5.0.21.0 | 2009.12.14 | Backdoor.FlyAgent.ARB |
| File size: 1400551 bytes |
| MD5...: d7435879a170e839eeeadb9587d68981 |
| SHA1..: 9a3727f6a25d14677840d6d578b4b6d1a1c3ec34 |
| SHA256: dd51f7f1837ef38987da140bcf303a0a0a064c4a6d7a11bb328fa1de64fd286b |
| ssdeep: 24576:bC7ATPZDzinZzdQq3D15pUylF83H3PFD+jIOnyCJqhQWodPjD4crbtZ0Jr hVpsdW:b8QZDzinZzV3J5e623fFD+jxy1hw/JrA |
| PEiD..: - |
| PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x1317 timedatestamp.....: 0x59bffa3 (Mon Dec 25 05:33:23 1972) machinetype.......: 0x14c (I386) ( 5 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x51ec 0x6000 7.00 4dba398236e8347fce073f48550e19c5 .rdata 0x7000 0xa4a 0x1000 3.58 367b7ce38d0c4c17f01e370dc697df5b .data 0x8000 0x1f58 0x2000 4.58 caf81b709a3fafbe71d2fc52d70be6a7 .data 0xa000 0x65000 0x65000 7.99 fcf40bcc3fc86886c00147009a3ba0ef .rsrc 0x6f000 0x3bf0 0x4000 3.40 825a8015620dc174a1747b2d60c4feb4 ( 2 imports ) > KERNEL32.dll: GetProcAddress, LoadLibraryA, CloseHandle, WriteFile, CreateDirectoryA, GetTempPathA, ReadFile, SetFilePointer, CreateFileA, GetModuleFileNameA, GetStringTypeA, LCMapStringW, LCMapStringA, HeapAlloc, HeapFree, GetModuleHandleA, GetStartupInfoA, GetCommandLineA, GetVersion, ExitProcess, HeapDestroy, HeapCreate, VirtualFree, VirtualAlloc, HeapReAlloc, TerminateProcess, GetCurrentProcess, UnhandledExceptionFilter, FreeEnvironmentStringsA, FreeEnvironmentStringsW, WideCharToMultiByte, GetEnvironmentStrings, GetEnvironmentStringsW, SetHandleCount, GetStdHandle, GetFileType, RtlUnwind, GetCPInfo, GetACP, GetOEMCP, MultiByteToWideChar, GetStringTypeW > USER32.dll: MessageBoxA, wsprintfA ( 0 exports ) |
| RDS...: NSRL Reference Data Set - |
| trid..: Win32 Executable MS Visual C++ (generic) (62.9%) Win32 Executable Generic (14.2%) Win32 Dynamic Link Library (generic) (12.6%) Clipper DOS Executable (3.3%) Generic Win/DOS Executable (3.3%) |
| pdfid.: - |
| <a href='http://info.prevx.com/aboutprogramtext.asp?PX5=88F072F6E75692145ED21559B9146E0008F29E40' target='_blank'>http://info.prevx.com/aboutprogramtext.asp?PX5=88F072F6E75692145ED21559B9146E0008F29E40</a> |
| ThreatExpert info: <a href='http://www.threatexpert.com/report.aspx?md5=d7435879a170e839eeeadb9587d68981' target='_blank'>http://www.threatexpert.com/report.aspx?md5=d7435879a170e839eeeadb9587d68981</a> |
| sigcheck: publisher....: n/a copyright....: n/a product......: n/a description..: n/a original name: n/a internal name: n/a file version.: n/a comments.....: n/a signers......: - signing date.: - verified.....: Unsigned |
| packers (Authentium): PE-Crypt.CF |
| packers (F-Prot): PE-Crypt.CF |
recycled.exe文件大小与DCIM.EXE相同,应该是同一病毒。
在L:/RECYCLER/S-5-3-42-2819952290-8240758988-879315005-3665中发现名为jwgkvsq.vmx的文件,
用FileInfo提取病毒文件信息:
文件说明符 : L:/RECYCLER/S-5-3-42-2819952290-8240758988-879315005-3665/jwgkvsq.vmx
属性 : -SHR
数字签名:否
PE文件:是
获取文件版本信息大小失败!
创建时间 : 2008-7-13 15:15:11
修改时间 : 2008-4-15 2:0:0
大小 : 160864 字节 157.96 KB
MD5 : 6b54e187a3a6971ffe03e9aea5afcacc
SHA1: 4809E42763DD2488DF993D752295941C0028085E
CRC32: 1997b4ea
上传到 http://www.virustotal.com扫描,结果如下:
| 反病毒引擎 | 版本 | 最后更新 | 扫描结果 |
| a-squared | 4.5.0.43 | 2009.12.15 | Net-Worm.Win32.Kido!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.12.15 | Win32/Conficker.worm.Gen |
| AntiVir | 7.9.1.108 | 2009.12.15 | TR/Crypt.ZPACK.Gen |
| Antiy-AVL | 2.0.3.7 | 2009.12.15 | Worm/Win32.Kido.gen |
| Authentium | 5.2.0.5 | 2009.12.02 | W32/Conficker!Generic |
| Avast | 4.8.1351.0 | 2009.12.15 | Win32:Confi |
| AVG | 8.5.0.427 | 2009.12.15 | I-Worm/Generic.CMN |
| BitDefender | 7.2 | 2009.12.15 | Win32.Worm.Downadup.Gen |
| CAT-QuickHeal | 10.00 | 2009.12.15 | Worm.Conficker.b |
| ClamAV | 0.94.1 | 2009.12.15 | Worm.Downadup-85 |
| Comodo | 3251 | 2009.12.15 | NetWorm.Win32.Kido.ih |
| DrWeb | 5.0.0.12182 | 2009.12.15 | Win32.HLLW.Autoruner.5555 |
| eSafe | 7.0.17.0 | 2009.12.14 | Win32.Banker |
| eTrust-Vet | 35.1.7176 | 2009.12.15 | Win32/Conficker |
| F-Prot | 4.5.1.85 | 2009.12.14 | W32/Conficker!Generic |
| F-Secure | 9.0.15370.0 | 2009.12.15 | Worm:W32/Downadup.gen!A |
| Fortinet | 4.0.14.0 | 2009.12.15 | W32/Conficker.B!worm |
| GData | 19 | 2009.12.15 | Win32.Worm.Downadup.Gen |
| Ikarus | T3.1.1.74.0 | 2009.12.15 | Net-Worm.Win32.Kido |
| Jiangmin | 13.0.900 | 2009.12.15 | Worm/Kido.fi |
| K7AntiVirus | 7.10.920 | 2009.12.14 | Net-Worm.Win32.Kido |
| Kaspersky | 7.0.0.125 | 2009.12.15 | Net-Worm.Win32.Kido.ih |
| McAfee | 5832 | 2009.12.14 | W32/Conficker.worm.gen.b |
| McAfee+Artemis | 5832 | 2009.12.14 | W32/Conficker.worm.gen.b |
| McAfee-GW-Edition | 6.8.5 | 2009.12.15 | Trojan.Crypt.ZPACK.Gen |
| Microsoft | 1.5302 | 2009.12.15 | Worm:Win32/Conficker.C |
| NOD32 | 4689 | 2009.12.15 | a variant of Win32/Conficker.X |
| Norman | 6.04.03 | 2009.12.15 | W32/Conficker.JA |
| nProtect | 2009.1.8.0 | 2009.12.15 | Worm/W32.Kido.160864 |
| Panda | 10.0.2.2 | 2009.12.14 | W32/Conficker.C.worm |
| PCTools | 7.0.3.5 | 2009.12.15 | Net-Worm.Kido!sd6 |
| Prevx | 3.0 | 2009.12.15 | High Risk Worm |
| Rising | 22.26.01.01 | 2009.12.15 | Hack.Exploit.Win32.MS08-067.hm |
| Sophos | 4.48.0 | 2009.12.15 | Mal/Conficker-A |
| Sunbelt | 3.2.1858.2 | 2009.12.15 | Trojan.Malware |
| Symantec | 1.4.4.12 | 2009.12.15 | W32.Downadup.B |
| TheHacker | 6.5.0.2.093 | 2009.12.15 | W32/Kido.ih |
| TrendMicro | 9.100.0.1001 | 2009.12.15 | WORM_DOWNAD.AD |
| VBA32 | 3.12.12.0 | 2009.12.15 | Worm.Win32.kido.92 |
| ViRobot | 2009.12.15.2089 | 2009.12.15 | Worm.Win32.Conficker.160864 |
| VirusBuster | 5.0.21.0 | 2009.12.14 | Worm.Kido.LA |
| File size: 160864 bytes |
| MD5...: 6b54e187a3a6971ffe03e9aea5afcacc |
| SHA1..: 4809e42763dd2488df993d752295941c0028085e |
| SHA256: 11fc18dbe7d497003d44beb4114a5c939bc3d95fc7ee05abbffb38af96f9d1a2 |
| ssdeep: 3072:RpovBKzUrgi1FDHDmTl8jAqJDdUMSk/+0zNQoiOuAhoIOM6+1u5lTTZuLEl :R+MwrguHDmTl8E2+q2MQoiza6os |
| PEiD..: - |
| PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x43eb timedatestamp.....: 0x3be8e4db (Wed Nov 07 07:38:03 2001) machinetype.......: 0x14c (I386) ( 4 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x3494 0x3600 6.28 da6b6d517febce744574317d6cd01268 .rdata 0x5000 0x74a 0x800 4.66 7ba7d50f2f5e74b4273df1570aa7022a .data 0x6000 0xfc18 0xf600 7.98 32c3b469093c428939e2d700e8026b1e .reloc 0x16000 0x9f6 0xa00 6.35 6be06ddaa058c48c14eb94c47e317bbe ( 7 imports ) > KERNEL32.dll: IsDBCSLeadByte, LoadLibraryA, InterlockedDecrement, InterlockedExchangeAdd, GetModuleFileNameA, GetProcAddress, Sleep, MulDiv, GetLocalTime, VirtualAlloc, VirtualProtect, DosDateTimeToFileTime, QueryPerformanceFrequency, IsDebuggerPresent, GetLastError, IsBadWritePtr, GetComputerNameA, GetUserDefaultLCID, IsBadReadPtr > USER32.dll: IsIconic, GetAncestor, GetCursor, IsWindowUnicode, GetMenuContextHelpId, IsCharUpperA, GetWindowDC, IsClipboardFormatAvailable, GetForegroundWindow, GetGUIThreadInfo, GetParent, GetWindowPlacement, IsMenu, InSendMessage, CopyIcon, GetIconInfo, GetDlgItem > ADVAPI32.dll: GetUserNameA > MSVCRT.dll: _CIsinh, ldiv, _CIfmod, _adjust_fdiv, malloc, _initterm, free, memmove, _memccpy, _ultoa, time, ceil, ldexp, _pctype, _isctype, modf, __mb_cur_max, localeconv, div, _itoa, _CItanh, srand > GDI32.dll: GetPixel, GdiFlush, GetBitmapDimensionEx, GetStretchBltMode > ole32.dll: CoFileTimeNow, CoDosDateTimeToFileTime, CoRevertToSelf > SHELL32.dll: DuplicateIcon, - ( 0 exports ) |
| RDS...: NSRL Reference Data Set - |
| pdfid.: - |
| trid..: Win32 Executable Generic (38.4%) Win32 Dynamic Link Library (generic) (34.2%) Clipper DOS Executable (9.1%) Generic Win/DOS Executable (9.0%) DOS Executable Generic (9.0%) |
| <a href='http://info.prevx.com/aboutprogramtext.asp?PX5=D93EFFDB60D8DC83746002923A6753008F44CED1' target='_blank'>http://info.prevx.com/aboutprogramtext.asp?PX5=D93EFFDB60D8DC83746002923A6753008F44CED1</a> |
| ThreatExpert info: <a href='http://www.threatexpert.com/report.aspx?md5=6b54e187a3a6971ffe03e9aea5afcacc' target='_blank'>http://www.threatexpert.com/report.aspx?md5=6b54e187a3a6971ffe03e9aea5afcacc</a> |
| sigcheck: publisher....: n/a copyright....: n/a product......: n/a description..: n/a original name: n/a internal name: n/a file version.: n/a comments.....: n/a signers......: - signing date.: - verified.....: Unsigned |
| packers (Antiy-AVL): CrypToCrackPeProtector0.93 |
用WinRAR将病毒文件打包加密压缩后删除。






相关推荐
一个蠕虫源程序,有想看的可以自己分析一下。
lifecalendarworm挖矿蠕虫查杀工具 内含三款病毒查杀工具,都是国外知名软件,国内软件就不推荐了 Lifecalendarworm是一种恶意软件,也被称为"Life Calendar"或"LimeRAT",它是一种后门蠕虫,可以允许攻击者远程...
Win32/Conficker.AA ,也被称为W32/Worm.AHGV , Win32.Worm.Downadup ,净Worm.Win32.Kido.bg ,蠕虫: Win32/Conficker , W32/Conficker.worm.gen ,并末/ Conficker ,是一种恶意蠕虫病毒传播的电脑在当地的网络...
Dashy Worm 短跑蠕虫Unity多点触控游戏项目源码模版C# 支持Unity版本5.5.0f3及以上 描述 Dashy Worm 是一款有趣、令人上瘾的游戏,具有可爱的图形,可以让玩家玩上几个小时。游戏的目标非常简单:控制你的蠕虫通过在...
sql编程开发的worm蠕虫经典代码sql programming code developed by the classic worm worm
千年蠕虫(The Millennium Internet Worm)——后面简称worm,是一段script及程序组成的,它执行的功能是利用linux系统的某些远程漏洞,获取该系统的进入权限,并且将自身 复制到其上并继续繁殖。现在发现的worm是针对...
Storm Worm Process Injection from the Windows Kernel.
engine-worm.c
Simulating and optimising worm propagation algorithms
worm_algorithms 玩蠕虫算法和协同
Space worm
Worm.WhBoy
世界上第一个蠕虫,后来用C编写的源码,供学习参考之用.
Analysis report for storm worm && botnet
视频监控存储worm技术简介.doc
worm_downad.ad趋势&微软专杀工具,貌似趋势的用起来更快些 看到很多人都中了,特此附上我的解决方法: 这个病毒是局域网的蠕虫病毒,就是寄生在局域网的某台电脑上,然后通过局域网攻击其他电脑,试其他电脑的密码...
构建了一种新型IPv6网络蠕虫——V6-Worm,该蠕虫运用双层扫描策略,在子网内和子网间分别采用基于组播和基于域间路由协议路由前缀的扫描策略,并在此基础上建立了一种双层蠕虫传播模型(double layer model,DLM)来...
morris worm source code
蠕虫铲运机 将网络连续及其续作《成电子书格式。 如何使用 首先,您需要一个现代版本的 安装最新版本(不是LTS); 至少需要v12.10.0。 然后,打开一个终端( , )并通过键入以下内容安装程序 npm install -g worm...
网上找的一个蠕虫代码,对本机影响而以,不会对网络造成影响,研究一下之后可以.不过请注意,我每次运行之后都是把改善出的东西删除了,因为实际作用要在重启之后才会发生作用.慎用!